Introduction
In our previous blog post, we explored the critical relationship between assessment security and validity in the context of online and remote assessments. We discussed the threats posed to assessment security, including impersonation, unauthorized materials, online cheating, and content leakage. Now, in this follow-up post, we will delve into the concrete measures that can be taken to mitigate these threats. By implementing robust security protocols and best practices, we can protect the integrity of online and remote assessments, ensuring the validity and trustworthiness of assessment results.
Mitigating Impersonation
Two-factor authentication
Implementing a two-factor authentication process adds an extra layer of security to verify the identity of test-takers. Two-factor authentication, also known as 2FA or multi-factor authentication, requires individuals to provide two different types of credentials to access the assessment platform. The first factor is typically something the test-taker knows, such as a password or a personal identification number (PIN). The second factor is something they possess, which could be a physical device like a smartphone or a token.
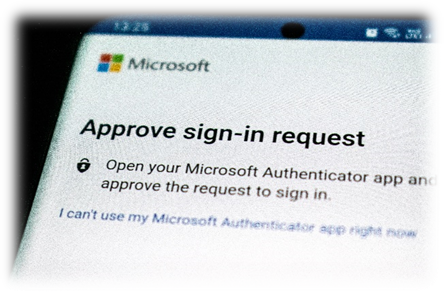
When test-takers initiate the login process, they are prompted to enter their username and password as the first authentication factor. Once the initial credentials are validated, the system then requires the second factor to establish their identity securely. Common methods for the second factor include a unique code sent to the test-taker’s registered mobile device via SMS or an authentication app, a physical token with a changing code, or even biometric authentication like a fingerprint or facial recognition.
For example, a test-taker logging into an assessment platform may first enter their username and password. After successful verification of the first factor, the system may send a one-time code to their mobile device. The test-taker then enters this code to complete the authentication process and gain access to the assessment.
By requiring both factors for authentication, the likelihood of fraudulent test-taking is significantly reduced. Even if someone manages to obtain the test-taker’s password, they would still need physical possession of their registered device or unique biometric information to pass the second factor. This added layer of security strengthens the integrity of the assessment process and ensures that only authorized individuals can access the assessments.
Identity verification services
Third-party identity verification services play a crucial role in ensuring that the individual taking the assessment is indeed the authorized test-taker. These services employ advanced technologies such as biometric authentication, facial recognition, voice recognition, or keystroke dynamics analysis to establish and verify the test-taker’s identity.

Biometric authentication is a common method used by identity verification services. It involves the use of unique biological characteristics of the test-taker, such as fingerprints or facial features, to confirm their identity securely. For instance, during the authentication process, the test-taker may be required to provide a fingerprint sample using a biometric scanner or undergo facial recognition scanning using a webcam. The system then compares these biometric features against pre-registered data to ensure a match.
Apart from biometrics, other methods like voice recognition or keystroke dynamics analysis can also be utilized. Voice recognition analyzes the unique characteristics of an individual’s voice, such as pitch, tone, and speech patterns, to verify their identity. Keystroke dynamics analysis, on the other hand, examines the typing patterns and rhythm of a person’s keystrokes to establish their identity.
By employing these identity verification services, assessment providers can ensure that only the authorized test-taker is accessing the assessment. This significantly reduces the chances of impersonation and helps maintain the integrity and fairness of the assessment process.
Remote proctoring
Remote proctoring is an effective solution that leverages AI algorithms and video monitoring to detect suspicious behaviors and maintain the integrity of the assessment process. With remote proctoring, proctors can remotely observe test-takers in real-time through video feeds, allowing them to identify potential impersonators or irregularities during the assessment.

Remote proctoring tools provide various features to monitor test-takers and their surroundings. Screen monitoring allows proctors to view the test-taker’s computer screen to ensure they are not accessing unauthorized resources or attempting to cheat by searching for answers. Webcam monitoring enables proctors to visually observe the test-taker and their immediate surroundings, ensuring that no prohibited materials or individuals are present.
In addition to visual monitoring, remote proctoring may include audio monitoring capabilities. Proctors can listen to the audio feed from the test-taker’s microphone to detect any suspicious conversations or signals of external assistance. AI algorithms play a vital role in remote proctoring by analyzing the video and audio feeds for potential cheating behaviors. These algorithms can detect patterns such as eye movements, head gestures, or unusual activity on the screen, alerting proctors to investigate further. Some advanced systems even employ facial recognition technology to match the test-taker’s face against their registered identity.
By using remote proctoring, assessment providers can deter and identify cheating attempts during online assessments. The presence of remote proctoring acts as a deterrent, as test-takers are aware that their activities are being monitored. It helps maintain fairness, credibility, and the validity of assessment results, ensuring that individuals are evaluated based on their own abilities and knowledge.
Preventing Unauthorized Materials
Secure browser lockdown
A secure browser environment is an effective measure to prevent test-takers from accessing unauthorized materials during an assessment. When test-takers launch the assessment, they are required to use a secure browser that restricts access to other applications and websites on their device. This lockdown ensures that the assessment remains the sole focus of their attention, eliminating the possibility of using external resources to gain an unfair advantage.

Secure browser software provides several features to maintain a controlled testing environment. It can disable keyboard shortcuts, preventing test-takers from using functions like copy and paste or opening new browser tabs. This restriction prevents them from easily accessing or searching for answers from external sources. Additionally, secure browsers can block access to specific websites or restrict internet connectivity altogether, further reducing the chances of using unauthorized materials.
By confining test-takers to a secure browser environment, assessment providers can significantly minimize the risk of cheating or using external resources during the assessment. This ensures that test results reflect the individual’s true knowledge and abilities.
Remote monitoring
Remote monitoring solutions play a crucial role in deterring the use of unauthorized materials during online assessments. These solutions enable proctors to observe test-takers via video feeds in real-time, providing an additional layer of supervision and accountability.
Proctors using remote monitoring can visually verify the test environment to ensure that no unauthorized materials or resources are present. They can scrutinize the test-taker’s physical surroundings, checking for printed notes, textbooks, or cheat sheets that could provide an unfair advantage. By having a clear view of the test-taker’s workspace, proctors can identify any suspicious objects or behaviors that may indicate the use of unauthorized materials.
In addition to visual monitoring, remote monitoring solutions may also offer screen-sharing capabilities. Proctors can remotely view the test-taker’s computer screen, allowing them to monitor their activities and ensure that no unauthorized software or files are being accessed.
The presence of remote monitoring acts as a deterrent, as test-takers are aware that their actions are being observed. This significantly reduces the temptation to use unauthorized materials during the assessment and promotes a fair testing environment.
Randomized question banks
Randomized question banks are an effective strategy to prevent the effectiveness of using pre-prepared unauthorized materials. Instead of relying on a fixed set of questions, assessment providers develop a large pool of questions that cover the required topics and concepts. Each time a test-taker initiates an assessment, a unique set of questions is randomly generated from this question bank.
By utilizing randomized question banks, assessment providers ensure that no two assessments are the same. This makes it much more challenging for test-takers to benefit from pre-existing materials or answer keys. Even if they have access to unauthorized resources, the specific questions and answer choices will likely differ from what they have prepared, diminishing the advantage of using external materials.
Randomized question banks promote fairness and integrity in the assessment process. Test-takers must rely on their own knowledge, understanding, and critical thinking skills to answer questions accurately. This approach encourages a deeper understanding of the subject matter and reduces the impact of unauthorized resources on assessment outcomes.
Combating Online Cheating
AI-powered plagiarism detection
Plagiarism detection software, powered by AI algorithms, is a powerful tool in combating online cheating during assessments. This software compares the test responses of individual test-takers with an extensive database of online sources, academic papers, and previous submissions. By analyzing similarities in wording, sentence structure, and content, the AI-powered software can identify instances of direct copying or paraphrasing from external resources.

The AI algorithms used in plagiarism detection software are designed to identify even subtle forms of plagiarism. They can detect similarities in text that may not be easily recognizable to human observers. The software flags sections of the test responses that match existing sources, indicating potential instances of plagiarism or unoriginal content.
By employing AI-powered plagiarism detection, assessment providers can discourage test-takers from submitting plagiarized or unoriginal responses. This technology serves as a deterrent, promoting academic integrity and ensuring that assessments accurately reflect the individual’s knowledge and understanding.
Time limits and item shuffling
Implementing time limits and randomizing the order of questions and answer choices are effective strategies to combat online cheating. Time limits create a sense of urgency and restrict the amount of time test-takers have to search for answers or seek assistance during the assessment.
By setting time limits, assessment providers create a challenging environment that requires test-takers to demonstrate their knowledge and problem-solving skills within a specific timeframe. This discourages reliance on external resources and encourages test-takers to rely on their own understanding and abilities.
In addition to time limits, shuffling the order of questions and answer choices adds another layer of complexity. When questions and answer choices are presented in a random order, test-takers cannot predict or anticipate the sequence of questions or the position of correct answers. This makes it difficult to rely on pre-existing knowledge or patterns to answer questions correctly.
The combination of time limits and item shuffling disrupts cheating strategies that rely on external resources or memorization techniques. Test-takers are more likely to engage with the assessment using their own knowledge and critical thinking skills, leading to a fair and accurate evaluation of their abilities.
Preventing Content Leakage
Enhanced encryption and secure storage
Preventing content leakage requires robust measures to protect assessment materials from unauthorized access. Employing strong encryption protocols for storing assessment content adds a layer of security that makes it significantly harder for unauthorized parties to intercept or decipher the materials. Encryption transforms the content into unreadable data that can only be accessed with the appropriate decryption key.

By utilizing encryption, assessment providers ensure that even if the content is somehow accessed without authorization, it remains indecipherable and unusable. This greatly reduces the risk of content leakage, as the stolen data would be of no value to unauthorized individuals.
In addition to encryption, using secure storage systems with access controls and audit trails further enhances content protection. Access controls restrict access to the assessment materials to only authorized individuals who have the necessary credentials and permissions. This ensures that only trusted personnel can view or modify the content. Audit trails keep a record of any activities related to the assessment materials, allowing for traceability and accountability.
Need-to-know access privileges
Limiting access to assessment materials to only those who require it based on their roles and responsibilities is a critical practice in preventing content leakage. Granting access privileges on a need-to-know basis ensures that only authorized personnel can access the assessment content, reducing the number of individuals with potential access to sensitive materials.
By implementing need-to-know access privileges, assessment providers minimize the risk of insider threats. Insider threats can occur when individuals with authorized access misuse or leak assessment materials. By restricting access to only those who genuinely require it for their specific tasks, the likelihood of unauthorized disclosure or misuse is significantly reduced.
Implementing strict access controls includes authentication mechanisms such as unique usernames and passwords, multi-factor authentication, and role-based access control (RBAC). RBAC allows assessment providers to define and assign specific roles and permissions to individuals based on their job functions. This ensures that each individual has the appropriate level of access and prevents unauthorized access to sensitive content.
Regular security audits
Regular security audits play a crucial role in preventing content leakage by identifying vulnerabilities and weak points in assessment systems. Conducting routine audits helps assess the security infrastructure, protocols, and practices in place and allows organizations to proactively address any potential gaps or vulnerabilities.
Security audits may involve various measures such as penetration testing, which simulates real-world attacks to identify vulnerabilities in the system. Vulnerability assessments help identify weaknesses in the system’s security controls and configurations. By regularly conducting these assessments, assessment providers can stay ahead of potential threats and ensure the continuous improvement of their security measures.
Additionally, reviewing access controls and permissions during security audits helps verify that only authorized individuals have appropriate access to the assessment materials. This ensures that any changes in personnel or job roles are reflected in the access privileges, reducing the risk of unauthorized access and content leakage.
By consistently conducting security audits, assessment providers demonstrate their commitment to maintaining a secure environment and mitigating the risk of content leakage. It allows them to stay proactive in identifying and addressing security vulnerabilities before they can be exploited.
Takeaways
Mitigating threats to online and remote assessment security requires a multi-faceted approach. Implementing measures such as two-factor authentication, remote proctoring, secure browser lockdown, AI-powered plagiarism detection, and randomized question banks can significantly reduce the impact of impersonation, unauthorized materials, online cheating, and content leakage. By employing these concrete security measures, assessment providers can ensure that assessment results accurately reflect individuals’ abilities and knowledge, promoting fair and informed decision-making based on those results.
However, it is crucial to recognize that balancing security and test-taker experience is essential. While robust assessment security is necessary, it is equally important to create a positive and supportive test-taker experience. Striking the right balance between security measures and the overall test-taker experience is crucial to ensure fairness, engagement, and accurate assessment outcomes. In our next blog post, we will delve into how to strike this balance effectively.
In the meantime, explore the powerful and user-friendly assessment security and proctoring functionalities offered by Interactivo—an innovative online training and assessment platform meticulously crafted to cater to your diverse training and testing needs.

